Table of Contents
Modern Authentication in Microsoft 365 is based on OAuth 2.0. By using App registration, we can enable Users or automated Processes to do the following.
User self-service sync | Allow Users to download placeholder data for their Outlook signatures (Preferred method). |
Organization wide silent sync | Allow Administrators to download placeholder data for Outlook signatures on behalf of the Users. |
Outlook signature placeholder sync using a self-service shortcut
Important note: If your Outlook signature templates have placeholders and multiple user-attribute values corresponding to the placeholders are not available, the signature will not be displayed.
Administrators can use this approach to deploy a shortcut to the User’s start menu. You must deploy the shortcut as an administrator or SYSTEM.
After installation, when the user launches the shortcut, the WPSecure engine will sync data corresponding to the placeholders in the Outlook signatures to the User’s device.
The first step is to create an App registration in Entra ID.
Open Entra ID console (a.k.a. Azure Portal) https://portal.azure.com/ and click on new “New Registration“
Provide a name for the application. Make sure the name reflects the nature of the registration (User-driven).
Name | WPSecure Signature Data Sync (This can be anything descriptive) |
Supported account types | Accounts in this organizational directory only |
Redirect URI | http://localhost:5453 (Public client/native (mobile & desktop) |
Allow public client flow | Yes |
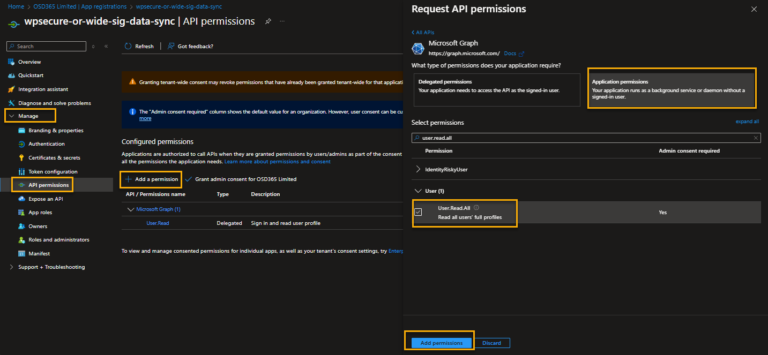
API Permissions | Microsoft Graph | User.Read (Permission type: Delegated) |
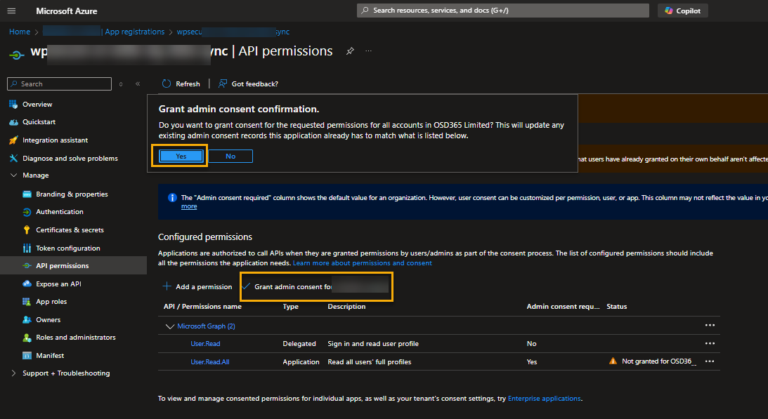
Admin Consent | Yes |
Open the newly created App registration and click “Manage/Authentication.“
Allow public client flow | Yes |
API Permissions | Microsoft Graph | User.Read (Permission type: Delegated) |
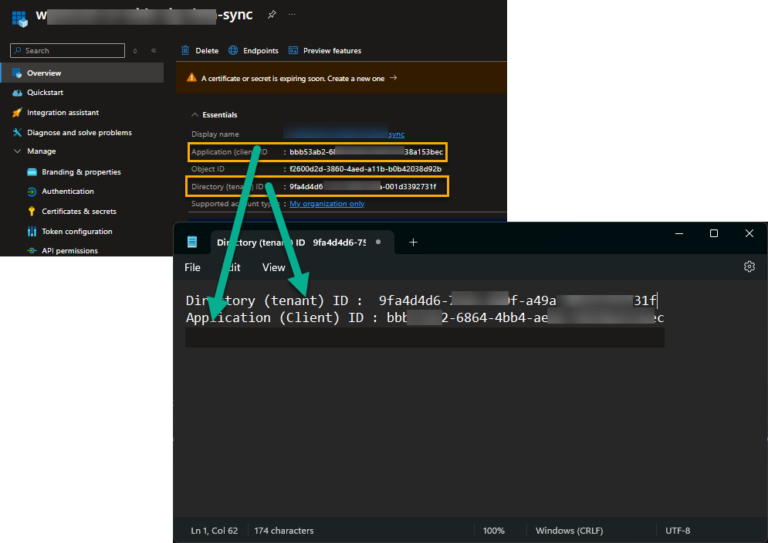
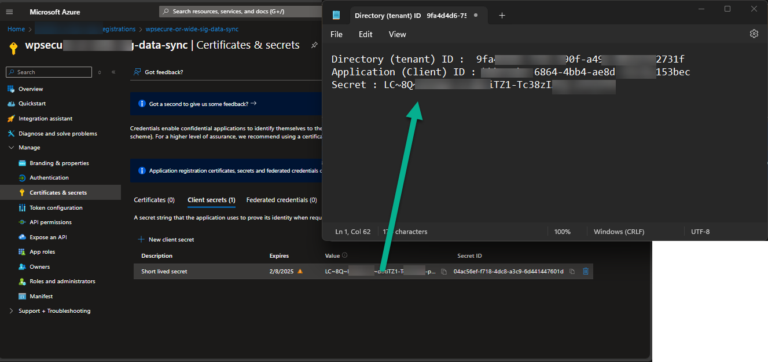
Copy the ClientID and the Tenant ID to Notepad.
That is it. Deploy the shortcut using the command below. Run the command as admin or SYSTEM when deploying via Intune/SCCM. Use the Tenant ID and Client ID values from Notepad.
wpsecure-set.exe -source azure -tenantid 9fb4d4d6-7541-490f-a49a-111d3393731f -clientid 55eba948-6cdd-4b98-ad9b-7ff7b36138c6 -createsc -version 1.2.3.5
The executable ‘wpsecure-set.exe‘ is in the WPSecure application directory within ProgramFiles (x86).
If the shortcut is deployed via Intune or SCCM, use the registry below to detect its presence or absence.
Key | HKEY_LOCAL_MACHINE\SOFTWARE\wpsecure |
Name | sssversion |
Value | 1.2.3.5 (Any value you choose. Formatted as Version) |
Organization wide Outlook signature placeholder silent sync
Administrators can use this approach to silently deploy Outlook signature placeholder data throughout the organization. The command must be run in the context of the logged-in user.
You could do this as a
- Win32 Intune APP
- SCCM application
- SCCM Package
- Baseline Script (Recommended)
There are two ways to deploy Outlook Signature placeholders silently.
Option 1: This option uses a ‘certificate’. We recommend performing the silent rollouts using Client certificates.
Option 2: This option uses a ‘Secret‘ key. So, it is more exposed than the first option. We recommend performing the rollout and immediately resetting the ‘Secret‘ after the placeholders are deployed.
Create a new App registration and provide a descriptive name. Click “Register“
Go to ‘Overview” and copy the Tenant ID and the Client ID to Notepad.
Using Client Certificates:
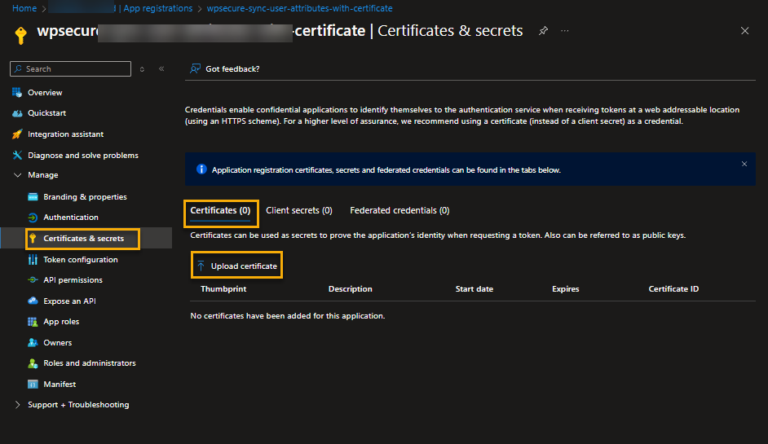
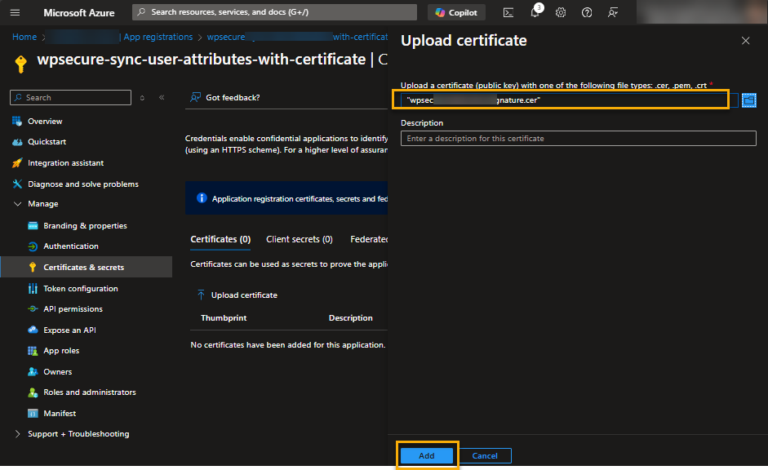
Go to ‘Manage/Certificate & secrets’ and click on the certificates tab. Then click ‘Upload certificate.’
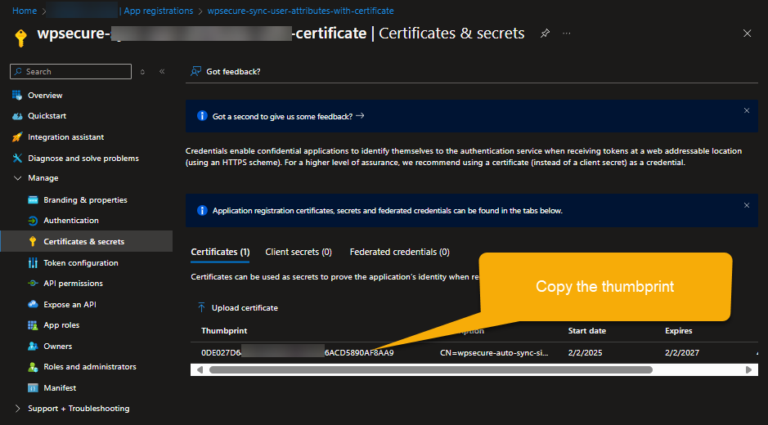
At the end of the process, copy the ‘thumbprint‘ to Notepad for future use.
Note: The certificate and its private key should be deployed as ‘non-exportable‘ to the ‘Current-Users‘ store on every device.
Skip the following step if you do not intend to use a Client ‘secret.’
Using Client Secret:
Go to ‘Manage/Certificate & secrets” and create a secret. Copy the secret to Notepad
1 | Keep the validity time span as short possible. |
2 | Deploy the Placeholder Sync process as an Intune Win32 App and not an open script. |
3 | After a successful deployment revoke or delete the secret from the App registration. |
API Permissions
Go to ‘Manage/API Permissions” and click “Add a permission.“
Click on “Grant admin consent.“
When using a Client Certificate
Run the following command in the standard Users context. Use the Tenant ID, Client ID, and thumbprint values from Notepad.
$startInfo = New-Object System.Diagnostics.ProcessStartInfo
$startInfo.FileName = "C:\Program Files (x86)\wpsecure\wpsecure-set.exe"
$startInfo.Arguments = "-source azure -tenantid 9faddg5d6-7541-490f-a49a-001d78492731f -clientid 45e353948-6cdd-4b98-ad9b-7ff634566038d4 -thumbprint 0DE027D6445464665905EF1DBC906ACD5890AF8AA9 -version 1.2.3.4"
$startInfo.WorkingDirectory = "C:\Program Files (x86)\wpsecure\"
$startInfo.UseShellExecute = $false
$startInfo.WindowStyle = [System.Diagnostics.ProcessWindowStyle]::Hidden
$startInfo.CreateNoWindow = $true
$scriptProcAD = New-Object System.Diagnostics.Process
$scriptProcAD.StartInfo = $startInfo
$scriptProcAD.Start() | Out-Null
$scriptProcAD.Close()
When using a Client Secret
Run the following command in the standard Users context. Use the Tenant ID, Client ID, and Secret values from Notepad.
$startInfo = New-Object System.Diagnostics.ProcessStartInfo
$startInfo.FileName = "C:\Program Files (x86)\wpsecure\wpsecure-set.exe"
$startInfo.Arguments = "wpsecure-set.exe -source azure -tenantid 9faddg5d6-7541-490f-a49a-001d78492731f -clientid 45e353948-6cdd-4b98-ad9b-7ff634566038d4 -secret NnS8Q~SOdoEdgdgdbghfbr0iIaIiwN345gdgssaugdhV -version 1.2.3.4"
$startInfo.WorkingDirectory = "C:\Program Files (x86)\wpsecure\"
$startInfo.UseShellExecute = $false
$startInfo.WindowStyle = [System.Diagnostics.ProcessWindowStyle]::Hidden
$startInfo.CreateNoWindow = $true
$scriptProcAD = New-Object System.Diagnostics.Process
$scriptProcAD.StartInfo = $startInfo
$scriptProcAD.Start() | Out-Null
$scriptProcAD.Close()
The executable ‘wpsecure-set.exe‘ is in the WPSecure application directory within the ProgramFiles (x86) directory.
The version is just your internal deployment identifier, which you would use if you were to deploy this using Software deployment tools like SCCM or Microsoft Intune.
Key | HKEY_CURRENT_USER\Software\Microsoft\Office\Outlook\wpsecure\signature |
Name | sddrversion |
Value | 1.2.3.4 (Any value you choose. Formatted as Version) |