Interactive retrieval of user attributes for Outlook signature placeholders
First lets check your Azure tenant type?
Public – The default Azure cloud used globally by commercial organizations and individuals.
China – A separate Azure instance operated by 21Vianet for compliance with Chinese regulations.
USGovernment / USGov – A sovereign Azure cloud designed for U.S. government agencies and contractors, offering enhanced compliance and security.
Suppose you are on a sovereign tenant like Azure China or Azure US Government. In that case, you will need to run one of the following commands before users can successfully connect to Azure using the shortcut to SYNC placeholder attributes.
"C:\Program Files (x86)\wpsecure\wpsecure-set.exe" -azauth china
"c:\Program Files (x86)\wpsecure\wpsecure-set.exe" -azauth usgovernment
If you want to move back to the Public tenant, you can reset the above set value by using the command below.
"c:\Program Files (x86)\wpsecure\wpsecure-set.exe" -azauth public
Setting up App Registration in EntraID
Open Entra ID console (a.k.a. Azure Portal) https://portal.azure.com/ and click on new “New Registration“
Provide a name for the application. Make sure the name reflects the nature of the registration (User-driven).
Name | WPSecure Signature Data Sync (This can be anything descriptive) |
Supported account types | Accounts in this organizational directory only |
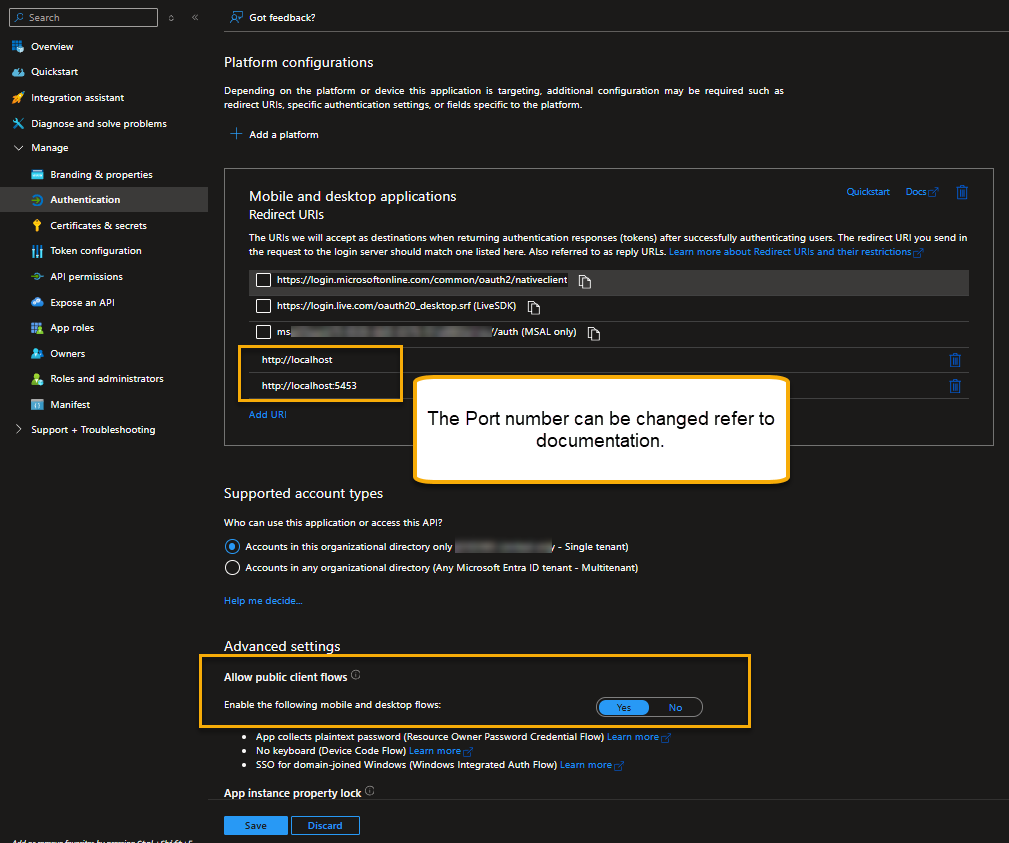
Redirect URI | http://localhost:5453 (Add new entry) http://localhost (Add new entry) |
Allow public client flow | Yes |
API Permissions | Microsoft Graph | User.Read (Permission type: Delegated) |
Admin Consent | Yes |
Open the newly created App registration and click “Manage/Authentication“, and then in “Manage/API Permissions“.
Allow public client flow | Yes |
API Permissions | Microsoft Graph | User.Read (Permission type: Delegated) |
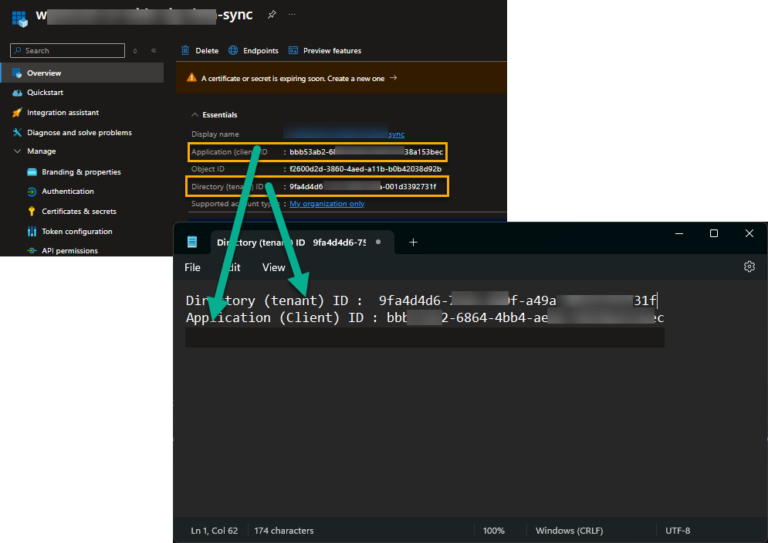
Copy the ClientID and the Tenant ID to Notepad.
That is it. Deploy the shortcut using the command below. Run the command as admin or SYSTEM when deploying via Intune/SCCM. Use the Tenant ID and Client ID values from Notepad.
"C:\Program Files (x86)\wpsecure\wpsecure-set.exe" -source azure -tenantid 9faddg5d6-1111-2222-a49a-001d78592732f -clientid 55eba948-6cdd-4b98-ad9b-7ff7b36138c6 -createsc -version 1.2.3.5
The executable ‘wpsecure-set.exe‘ is in the WPSecure application directory within ProgramFiles (x86).
If the shortcut is deployed via Intune or SCCM, use the registry below to detect its presence or absence.
Key | HKEY_LOCAL_MACHINE\SOFTWARE\wpsecure |
Name | sssversion |
Value | 1.2.3.5 (Any value you choose. Formatted as Version) |
Run the command below as an administrator to remove the shortcut above.
"c:\Program Files (x86)\wpsecure\wpsecure-set.exe" -smsssc